January PhishQueue Phishing News
“Phishing hides in plain sight…PhishQueue brings it to light.”
Microsoft Flags Multi-Stage Phishing and Business Email Compromise Attacks Targeting Organizations
The Growing Threat
What’s Going On?
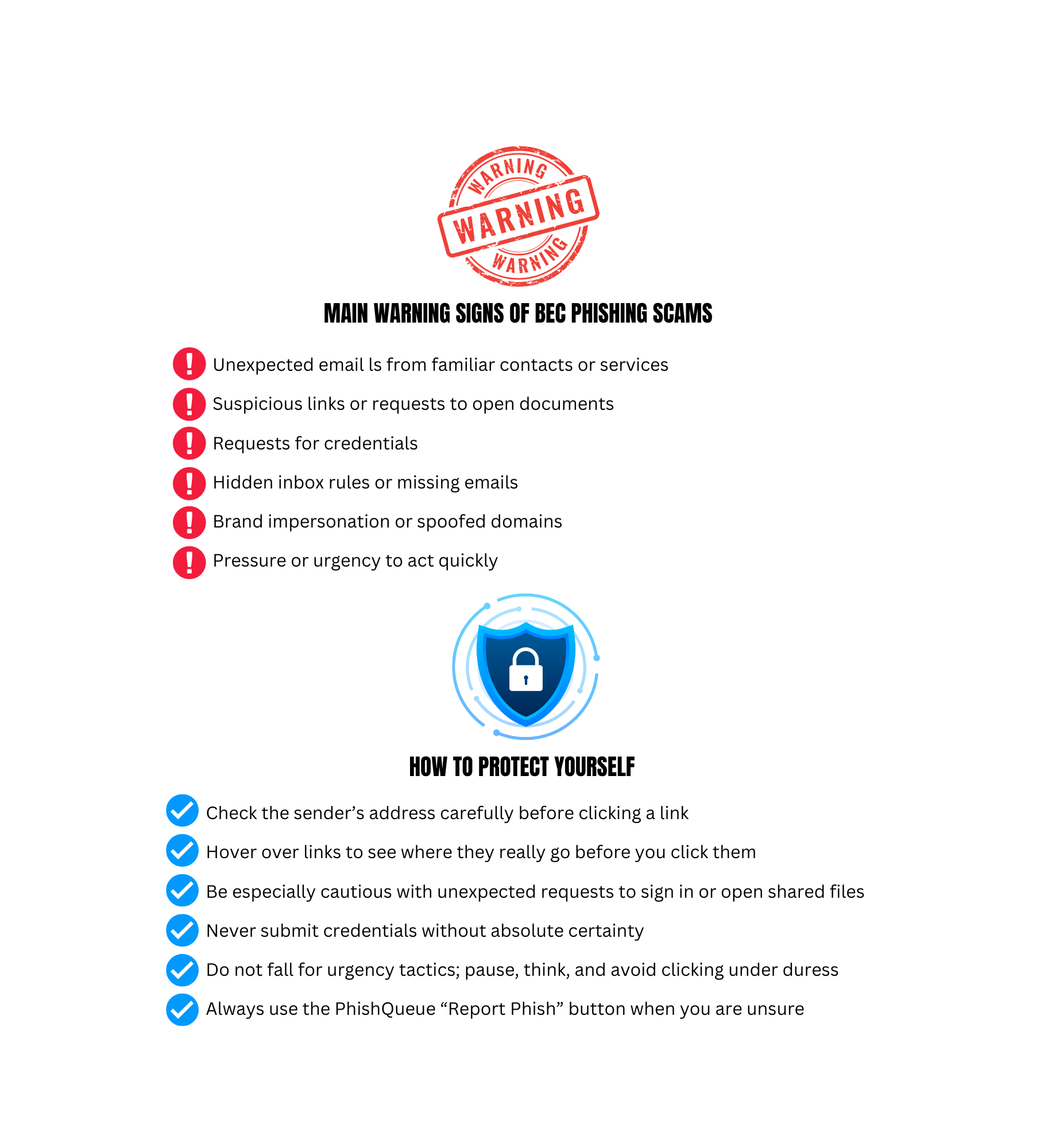
Security researchers at Microsoft have uncovered a sophisticated phishing campaign that starts with a deceptive email appearing to come from a trusted contact or familiar service. This attack leads to stolen login credentials and allows the attacker to create rules inside a victim’s email account that hide further malicious activity.
Because the messages originate from accounts that have already been compromised, they are more likely to look real and bypass basic security checks.
How It Works:
- An email arrives that seems legitimate, possibly from a coworker or a service you
- The message contains a link to what looks like a genuine document or shared file.
- When you click the link, you are taken to a fake login page and asked to enter your credentials.
- If you enter your email and password, attackers capture them.
- With access, attackers can create hidden inbox rules that hide evidence or remove incoming emails, then send further phishing messages from the compromised account.
Why It Is Dangerous:
- The phishing email may come from a familiar address, making it harder to spot.
- Once attackers control your account, they can send phishing messages to your contacts.
- Hidden inbox rules can prevent you from seeing new messages that might warn you something is wrong.
- Because attackers are already inside, simply resetting your password may not fully remove their access without additional cleanup.
Attackers can silently take over trusted email accounts, hide their activity, and spread phishing internally, turning one mistake into a widespread breach.
Sources: Microsoft Flags Phishing and BEC Attacks
🛡️ Your Best Defense: Do not click. Verify with Phishqueue.
If something feels even slightly wrong, submit the message to PhishQueue.
📌 Remember: PhishQueue will analyze the message for you and tell you if it is safe or malicious, with no risk to you.
_____________________________________
🤖 Fake Password Manager Support Emails
🔍 Example:Users of a popular password manager were targeted with fake ‘backup your vault’ emails designed to capture master passwords and all stored credentials.
🤖 Brand Impersonation Scams
🔍 Example: Research shows that attackers continue to impersonate major brands like Microsoft, Google, and Amazon to trick users into handing over login credentials.
🤖 Email Domain Spoofing
🔍 Example:Threat actors have exploited misconfigured email systems and routing to make phishing emails appear as if they came from inside an organization.
🚨 The Bottom Line
Phishing threats are becoming more dangerous.
👉 Stay safe with PhishQueue.
______________________________________________________
Quick Tips to Stay Safe:
- Pause Before You Click:If an email asks you to sign in or update information, think first.
- Check the Sender: Look at the full email address, not just the name that appears.
- Hover Over Links: Preview where links actually go before you click.
- Report to Phishquue: When in doubt, use the “Report Phish” button and let PhishQueue give you a safety verdict.
______________________________________________________
🎭 Phishing Joke of the Month
💡Why was the phishing email feeling confident?
👉 Because when it said ‘Trust me’, someone actually did. 😆
Cybersecurity is serious, but staying informed does not have to be dull!
Stay vigilant,
The PhishQueue Team