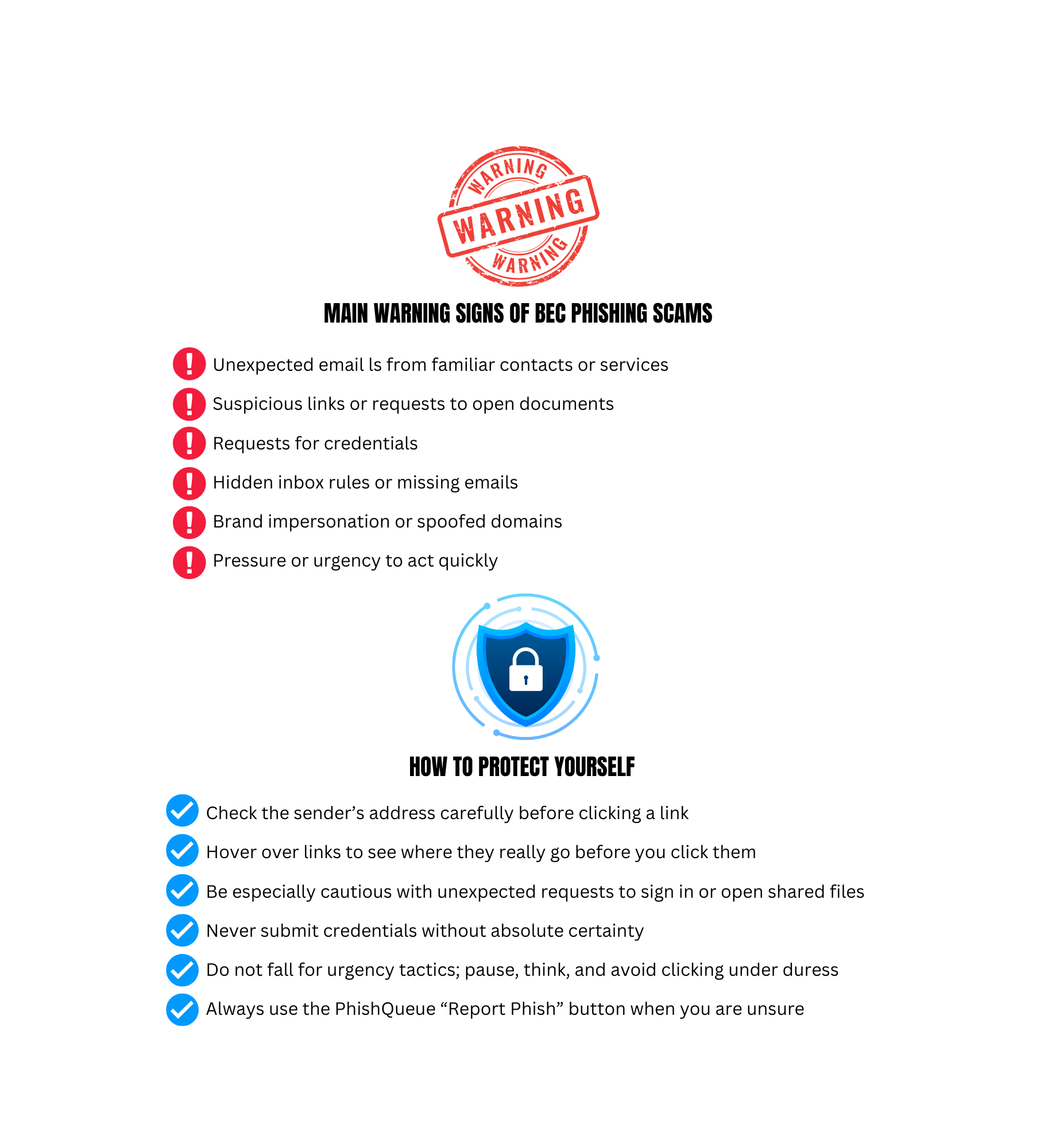
February 2026 Lunch N Learn
This event will be both educational and informative. Attendees are eligible to earn ISC2 and ISACA CPE credits by providing their membership numbers. Certificates for ISC2 and ISACA CPEs will be issued following the event. Speaker: G. Mark Hardy is the President of National Security Corporation and has been a trusted provider of information security […]